完成如何访问公司内网资源(外网如何访问公司内网)
时间:2024/7/15作者:未知来源:手揣网教程人气:
出差的或者休假的小伙伴如果说急需公司内部资料文件该如何实现呢,找同事帮忙传递吗?万一同事有事忙或者恰好这会有事出去了呢。这个时候就想能随时随地的访问公司内部的资源就好了。这个时候你要往下看啦接下来的文章也许能帮助到你
前言简介
VPN是什么:
VPN全称(Virtual Private Network)、中文译为:虚拟私人网络,又称为虚拟专用网络,用于在不安全的线路上安全的传输数据。
OpenVPN
一个实现VPN的开源软件,OpenVPN 是一个健壮的、高度灵活的 VPN 守护进程。它支持 SSL/TLS 安全、Ethernet bridging、经由代理的 TCP 或 UDP 隧道和 NAT。另外,它也支持动态 IP 地址以及DHCP,可伸缩性足以支持数百或数千用户的使用场景,同时可移植至大多数主流操作系统平台上。官网:https://openvpn.net, GitHub地址:https://github.com/OpenVPN/openvpn
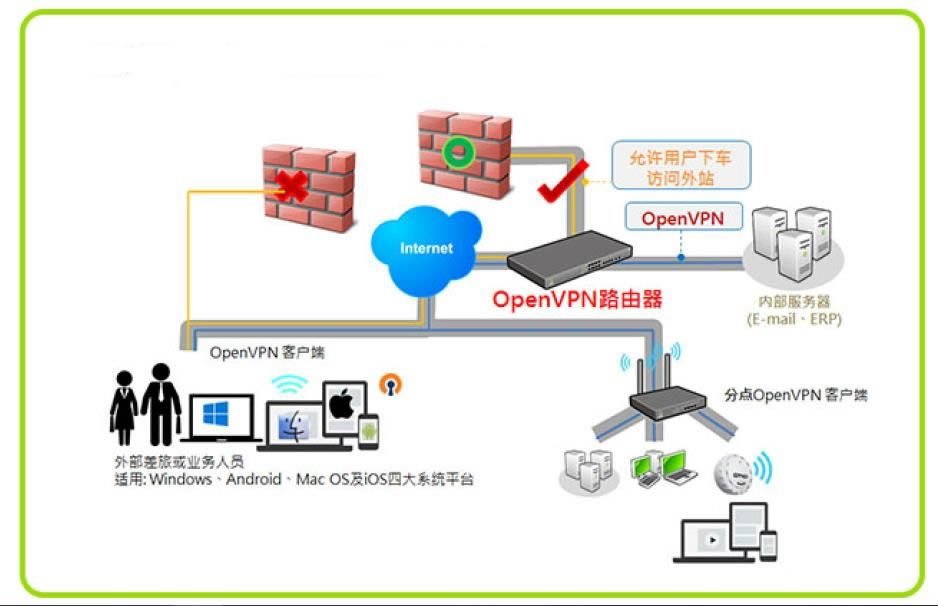
OpenVPN示意图
环境配置信息
openvpn server 192.168.154.13 10.0.20.20 web-server1: 10.0.20.100 # 操作系统版本: CentOS Linux release 7.9.2009OpenVPN安装
1、安装openvpn
这里采用yum安装方式来安装openvpn
[root@node03 ~]# yum -y install openvpn2、安装easy-rsa
从GitHub中下载easy-rsa GitHub地址为 https://github.com/OpenVPN/easy-rsa
2.1、下载easy-rsa包 并解压出来
# 创建目录专用于存放软件包 [root@node03 ~]# mkdir /app/openvpn -p [root@node03 openvpn]# wget https://github.com/OpenVPN/easy-rsa/archive/refs/heads/master.zip [root@node03 openvpn]# unzip master.zip [root@node03 openvpn]# mv easy-rsa-master easy-rsa2.2 配置openvpn
# 拷贝openVPN server配置模板文件到/etc/openvpn目录下 [root@node03 openvpn]# cp /usr/share/doc/openvpn-2.4.10/sample/sample-config-files/server.conf /etc/openvpn/ # 拷贝证书管理工具到/etc/openvpn下命名为easyrsa-server [root@node03 openvpn]# cp -a easy-rsa /etc/openvpn/easyrsa-server [root@node03 ~]# cd /etc/openvpn/easyrsa-server/ [root@node03 easyrsa-server]# cp easyrsa3/vars.example /etc/openvpn/easyrsa-server/easyrsa3/vars # 查看目录结构 [root@node03 ~]# cd /etc/openvpn/easyrsa-server/easyrsa3 [root@node03 easyrsa3]# tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── vars ├── vars.example └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 1 directory, 12 files [root@node03 easyrsa3]# # 修改vars配置文件根据自己当前环境配置以下几行 [root@node03 easyrsa3]# vim vars set_var EASYRSA_REQ_COUNTRY "CN" set_var EASYRSA_REQ_PROVINCE "Beijing" set_var EASYRSA_REQ_CITY "Haidian" set_var EASYRSA_REQ_ORG "mr.luo" set_var EASYRSA_REQ_EMAIL "admin@root.com" set_var EASYRSA_REQ_OU "My OpenVPN"3、初始化pki环境和CA签发机构
# 使用pwd查看当前所在路径 [root@node03 easyrsa3]# pwd /etc/openvpn/easyrsa-server/easyrsa3 # 生成pki目录用于保存证书 [root@node03 easyrsa3]# ./easyrsa init-pki Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easyrsa-server/easyrsa3/pki # 查看生成后的pki目录下的文件 [root@node03 easyrsa3]# ll pki/ total 16 -rw------- 1 root root 4616 4月 9 02:00openssl-easyrsa.cnf drwx------ 2 root root 38 4月 9 02:03 private drwx------ 2 root root 60 4月 9 02:58 reqs -rw------- 1 root root 4750 4月 9 02:00 safessl-easyrsa.cnf4、创建CA机构
# 创建ca证书 如果不想在后续签名中输入密码可以加上nopass 创建ca不使用密码 [root@node03 easyrsa3]# ./easyrsa build-ca Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Enter New CA Key Passphrase: #输入ca的密码 Re-Enter New CA Key Passphrase: #再次输入ca的密码 Generating RSA private key, 2048 bit long modulus ...............................................................+++ ...........................+++ e is 65537 (0x10001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]: #直接回车 CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /etc/openvpn/easyrsa-server/easyrsa3/pki/ca.crt #ca的公钥 # 验证CA的公钥 [root@node03 easyrsa3]# ll pki/ca.crt -rw------- 1 root root 1172 4月 9 02:01 pki/ca.crt # 验证CA的私钥 [root@node03 easyrsa3]# ll pki/private/ca.key -rw------- 1 root root 1766 1766 4月 9 02:01 pki/private/ca.key5、创建服务端证书(私钥)
[root@node03 easyrsa3]# ./easyrsa gen-req server nopass #生成server证书且不使用密码 Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key .......................................................................................... .........................................................................................+ writing new private key to '/etc/openvpn/easyrsa-server/easyrsa3/pki/easy-rsa-15024.cRlqdd #生成证书的临时文件 ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [server]: #直接回车 Keypair and certificate request completed. Your files are: req: /etc/openvpn/easyrsa-server/easyrsa3/pki/reqs/server.req #openvpn server req证书文件 key: /etc/openvpn/easyrsa-server/easyrsa3/pki/private/server.key #openvpn 私钥 # 验证CA证书 [root@node03 easyrsa3]# ll pki/private/ 总用量 8 -rw------- 1 root root 1766 4月 9 02:01 ca.key -rw------- 1 root root 1704 4月 9 02:03 server.key # 验证req文件 [root@node03 easyrsa3]# ll pki/reqs/ 总用量 4 -rw------- 1 root root 887 4月 9 02:03 server.req6、签发服务端证书
使用自建ca签发服务器证书,即生成服务端crt公钥,crt公钥后期将用户发送给客户端,从而实现与openvpn server端加密传输数据。
# 签发服务端证书,备注信息为server [root@node03 easyrsa3]# ./easyrsa sign server server Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a server certificate for 825 days: #证书有效时长 subject= commonName = server #通用名称 Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes #输入yes继续 Using configuration from /etc/openvpn/easyrsa-server/easyrsa3/pki/easy-rsa-15065.QeDHJH/tmp.L2GwRO Enter pass phrase for /etc/openvpn/easyrsa-server/easyrsa3/pki/private/ca.key: #输入ca密码后继续 Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'server' Certificate is to be certified until May 23 15:44:06 2022 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/server.crt # 验证生成的服务端公钥 [root@node03 easyrsa3]# ll /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/server.crt -rw------- 1 root root 4547 4月 9 02:04 /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/server.crt7、创建Diffie-Hellman
密钥交换方法,由惠特菲尔德·迪菲(Bailey Whitfield Diffie)、马丁·赫尔曼(Martin Edward Hellman)于1976年发表,它是一种安全协议,让双方在完全没有对方任何预先信息的条件下通过不安全信道建立起一个密钥,这个密钥一般作为“对称加密”的密钥而被双方在后续数据传输中使用,DH数学原理是base离散对数问题,做类似事情的还有非对称加密类算法,如:RSA。其应用非常广泛,在SSH、VPN、Https…都有应用,堪称现代密码基石。
[root@node03 easyrsa3]# ./easyrsa gen-dh Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time .......................................................................................+...............................+...........++*++* DH parameters of size 2048 created at /etc/openvpn/easyrsa-server/easyrsa3/pki/dh.pem # 验证生成的秘钥文件 [root@node03 easyrsa3]# ll /etc/openvpn/easyrsa-server/easyrsa3/pki/dh.pem -rw------- 1 root root 424 4月 9 02:04 /etc/openvpn/easyrsa-server/easyrsa3/pki/dh.pem8、创建客户端证书
# 创建客户端证书的存放目录 [root@node03 ~]# mkdir /app/openvpn/client -p # 复制客户端配置文件 [root@node03 ~]# cp /etc/openvpn/easyrsa-server/ /app/openvpn/client -a # 生成pki目录 [root@node03 easyrsa3]# cd /app/openvpn/client/easyrsa-server/easyrsa3 [root@node03 easyrsa3]# ./easyrsa init-pki Note: using Easy-RSA configuration from: /app/openvpn/client/easyrsa-server/easyrsa3/vars WARNING!!! You are about to remove the EASYRSA_PKI at: /app/openvpn/client/easyrsa-server/easyrsa3/pki and initialize a fresh PKI here. Type the word 'yes' to continue, or any other input to abort. Confirm removal: yes init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /app/openvpn/client/easyrsa-server/easyrsa3/pki # 验证pki目录 [root@node03 easyrsa3]# ll pki/ 总用量 16 -rw------- 1 root root 4616 4月 9 02:06 openssl-easyrsa.cnf drwx------ 2 root root 42 4月 9 02:57 private drwx------ 2 root root 42 4月 9 02:57 reqs -rw------- 1 root root 4820 4月 9 02:06 safessl-easyrsa.cnf [root@node03 easyrsa3]# ll ./pki/private/ 总用量 0 [root@node03 easyrsa3]# ll ./pki/reqs/ 总用量 0 # 生成客户端证书 [root@node03 easyrsa3]# ./easyrsa gen-req mr.luo Note: using Easy-RSA configuration from: /app/openvpn/client/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key ....................................+++ .........................................................................................................+++ writing new private key to '/app/openvpn/client/easyrsa-server/easyrsa3/pki/easy-rsa-1774.CZzEA5/tmp.Dfg4Cw' Enter PEM pass phrase: #输入密码 Verifying - Enter PEM pass phrase: #再次输入密码 ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [mr.luo]: Keypair and certificate request completed. Your files are: req: /app/openvpn/client/easyrsa-server/easyrsa3/pki/reqs/mr.luo.req key: /app/openvpn/client/easyrsa-server/easyrsa3/pki/private/mr.luo.key # 验证用户证书 [root@node03 easyrsa3]# tree pki/ pki/ ├── openssl-easyrsa.cnf ├── private │ └── mr.luo.key ├── reqs │ └── mr.luo.req └── safessl-easyrsa.cnf 2 directories, 4 files9、签发客户端证书
需要进入到openVPN server目录中签发客户端证书
[root@node03 easyrsa3]# cd /etc/openvpn/easyrsa-server/easyrsa3/ # server端导入req文件 [root@node03 easyrsa3]# ./easyrsa import-req /app/openvpn/client/easyrsa-server/easyrsa3/pki/reqs/mr.luo.req mr.luo Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 The request has been successfully imported with a short name of: mr.luo You may now use this name to perform signing operations on this request. # server端签发客户端证书 [root@node03 easyrsa3]# ./easyrsa sign client mr.luo Note: using Easy-RSA configuration from: /etc/openvpn/easyrsa-server/easyrsa3/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a client certificate for 825 days: subject= commonName = mr.luo Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes Using configuration from /etc/openvpn/easyrsa-server/easyrsa3/pki/easy-rsa-1874.R5ptap/tmp.5mEQRT Enter pass phrase for /etc/openvpn/easyrsa-server/easyrsa3/pki/private/ca.key: #输入ca的密码 Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'mr.luo' Certificate is to be certified until Jun 3 14:50:52 2022 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/mr.luo.crt # 验证签发后的crt证书 [root@node03 easyrsa3]# ll /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/mr.luo.crt -rw------- 1 root root 4432 4月 9 02:08 /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/mr.luo.crt10、复制证书到server目录
对签发的服务端证书进行归档保存
# 先创建相对应的目录 [root@node03 easyrsa3]# mkdir /etc/openvpn/certs [root@node03 easyrsa3]# cd /etc/openvpn/certs/ [root@node03 certs]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/dh.pem . [root@node03 certs]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/ca.crt . [root@node03 certs]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/server.crt . [root@node03 certs]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/private/server.key . # 验证证书目录下的文件 [root@node03 certs]# tree . ├── ca.crt ├── dh.pem ├── server.crt └── server.key 0 directories, 4 files11、客户端公钥和私钥
对签发好的客户端证书进行归档保存
# 创建客户端证书存放目录 [root@node03 certs]# mkdir /app/openvpn/client/mr.luo [root@node03 certs]# cd !$ cd /app/openvpn/client/mr.luo [root@node03 mr.luo]# ls [root@node03 mr.luo]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/ca.crt . [root@node03 mr.luo]# cp /etc/openvpn/easyrsa-server/easyrsa3/pki/issued/mr.luo.crt . [root@node03 mr.luo]# cp /app/openvpn/client/easyrsa-server/easyrsa3/pki/private/mr.luo.key . [root@node03 mr.luo]# tree . ├── ca.crt ├── mr.luo.crt └── mr.luo.key 0 directories, 3 files12、server端配置文件
# 先创建相对应的目录并授权相关用户权限 root@node03 mr.luo]# mkdir /var/log/openvpn [root@node03 mr.luo]# chown -R openvpn.openvpn /var/log/openvpn/ [root@node03 mr.luo]# chown -R openvpn.openvpn /etc/openvpn/ # 编辑openVPN配置文件 [root@node03 mr.luo]# vim /etc/openvpn/server.conf # 最终配置 [root@node03 mr.luo]# grep "^[a-Z]" /etc/openvpn/server.conf local 192.168.154.13 port 1194 proto tcp dev tun ca /etc/openvpn/certs/ca.crt cert /etc/openvpn/certs/server.crt key /etc/openvpn/certs/server.key dh /etc/openvpn/certs/dh.pem server 10.8.0.0 255.255.255.0 push "route 10.0.20.0 255.255.255.0" push "route 192.168.154.0 255.255.255.0" keepalive 10 120 cipher AES-256-CBC max-clients 200 user openvpn group openvpn persist-key persist-tun status openvpn-status.log log-append /var/log/openvpn/openvpn.log verb 9 mute 2013、配置iptables规则
# 关闭自带的firewalld服务 [root@node03 mr.luo]# systemctl stop firewalld [root@node03 mr.luo]# systemctl disable firewalld # 安装iptables服务如果不安装的话它的规则没法保存 [root@node03 mr.luo]# yum install iptables-services iptables -y [root@node03 mr.luo]# systemctl enable iptables.service [root@node03 mr.luo]# systemctl start iptables.service # 清空iptables规则 [root@node03 mr.luo]# iptables -F [root@node03 mr.luo]# iptables -X [root@node03 mr.luo]# iptables -Z [root@node03 mr.luo]# iptables -t nat -F [root@node03 mr.luo]# iptables -t nat -X [root@node03 mr.luo]# iptables -t nat -Z [root@node03 mr.luo]# iptables -t nat -A POSTROUTING -s 10.8.0.0/16 -j MASQUERADE [root@node03 mr.luo]# iptables -A INPUT -p TCP --dport 1194 -j ACCEPT [root@node03 mr.luo]# iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT [root@node03 mr.luo]# service iptables save iptables: Saving firewall rules to /etc/sysconfig/iptables:[ 确定 ] # 验证防火墙规则 [root@node03 mr.luo]# iptables -vnL Chain INPUT (policy ACCEPT 3891 packets, 436K bytes) pkts bytes target prot opt in out source destination 156K 148M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194 4408 4939K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED Chain FORWARD (policy ACCEPT 276K packets, 162M bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 150K packets, 35M bytes) pkts bytes target prot opt in out source destination [root@node03 mr.luo]# iptables -t nat -vnL Chain PREROUTING (policy ACCEPT 12055 packets, 682K bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 797 packets, 106K bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 89 packets, 6583 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 89 packets, 6583 bytes) pkts bytes target prot opt in out source destination 8562 445K MASQUERADE all -- * * 10.8.0.0/16 0.0.0.0/0 # 开启路由转发功能 [root@node03 mr.luo]# vim /etc/sysctl.conf net.ipv4.ip_forward = 1 [root@node03 mr.luo]# sysctl -p net.ipv4.ip_forward = 1 # 启动openVPN服务,并设置开机自启动 [root@node03 mr.luo]# systemctl start openvpn@server [root@node03 mr.luo]# systemctl enable openvpn@server14、安装window客户端
安装好之后在安装目录中有个sample-config目录,在里头找到client.opvn模板复制一份到config目录下然后修改其配置文件
client #声明自己是个客户端 dev tun #接口类型,必须和服务端保持一致 proto tcp #使用的协议,必须和服务端保持一致 remote 192.168.154.13 1194 #server端的ip和端口,可以写域名但是需要可以解析成IP resolv-retry infinite nobind persist-key # persist-tun ca ca.crt cert mr.luo.crt key mr.luo.key remote-cert-tls server #指定采用服务器校验方式 #tls-auth ta.key 1 cipher AES-256-CBC verb 32、从服务器中下载客户端所用的证书文件到config目录中
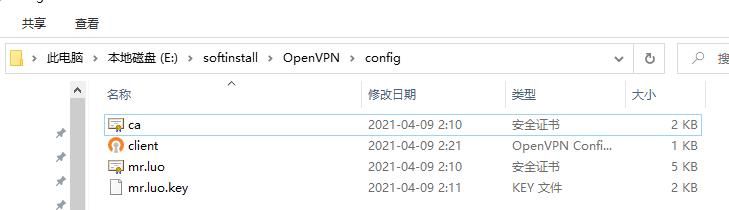
3、随后启动客户端与服务器端进行连接通信
输入在服务器端设置好的密码即可
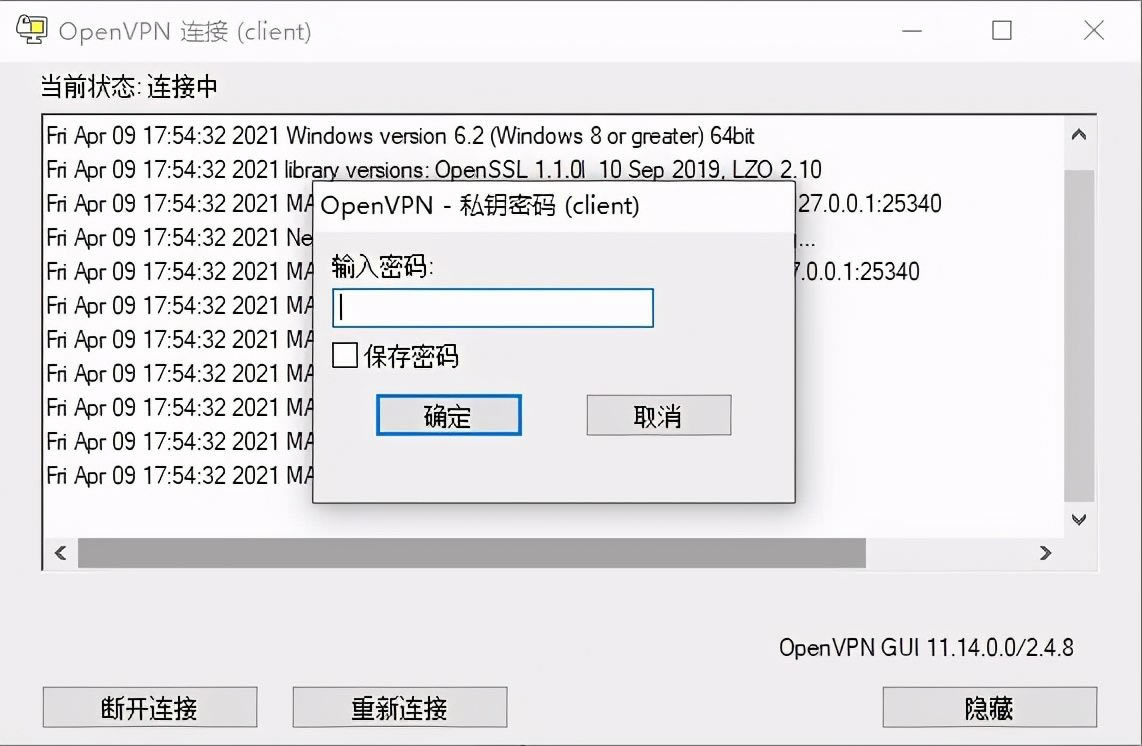
客户端登录界面
4、登录后显示的信息
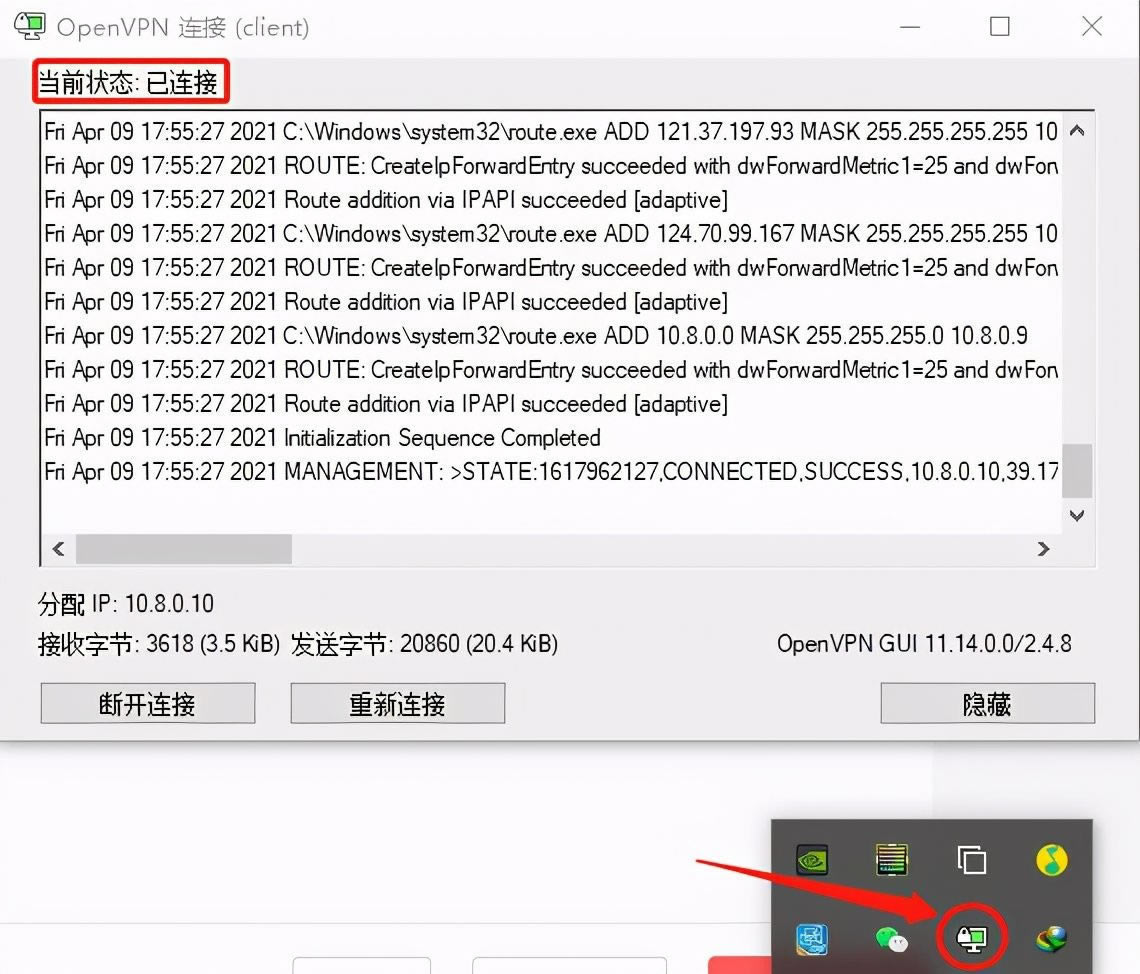
登录成功
5、最后就可以实现与公司之间的内网信息互通啦
关键词:完成如何访问公司内网资源(外网如何访问公司内网)